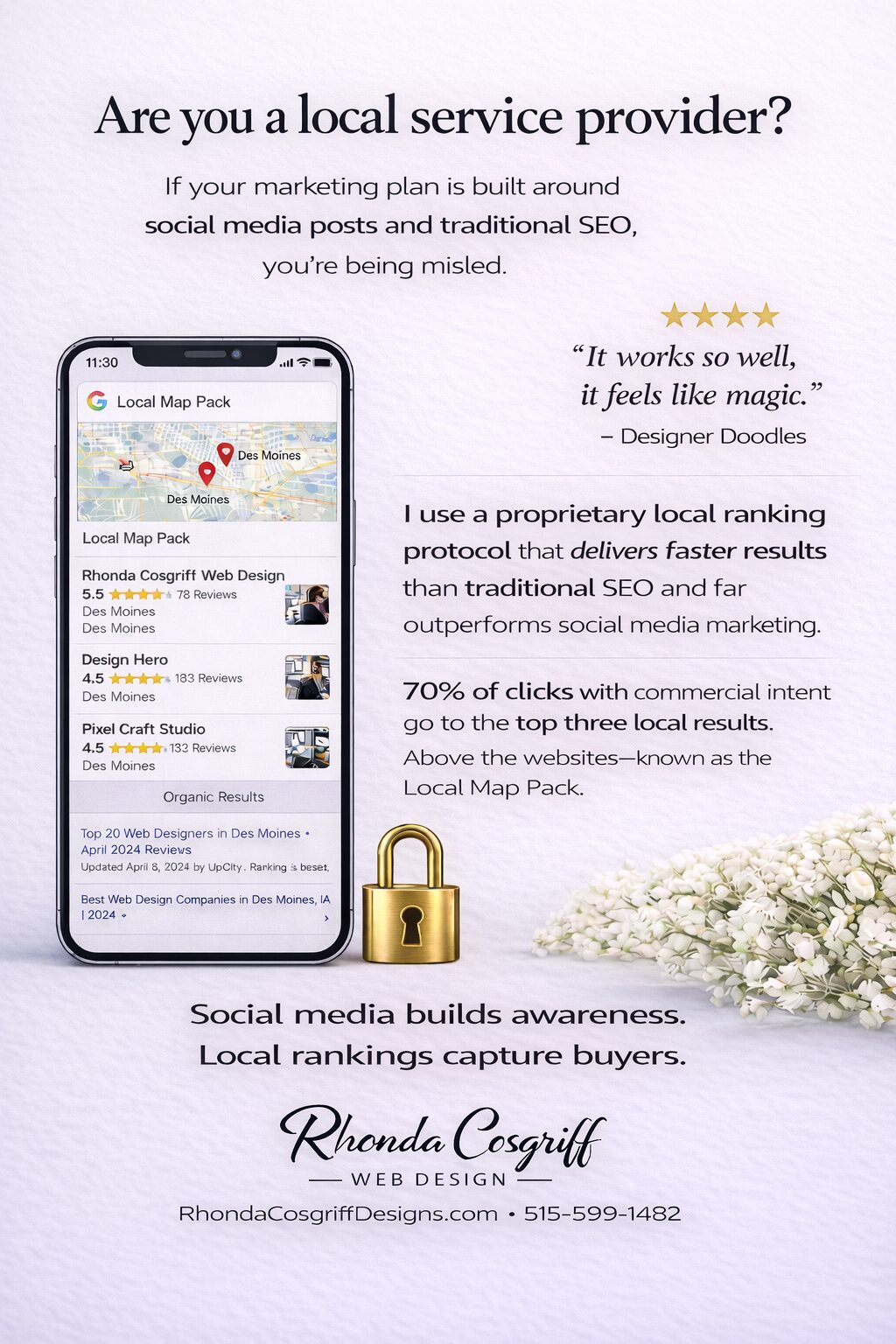
Security Models in Web Development: Protecting Your Digital Assets in 2025
As cyber threats continue to evolve in 2025, the need for robust security measures in web development has never been more critical. Traditional security models, which often rely on securing the perimeter of a network, are becoming less effective against modern, sophisticated threats. This is where the Zero Trust Security Model comes into play.
The Zero Trust model operates on the premise that no one—whether inside or outside the network—should be trusted by default. Every user, device, and system must continuously verify their identity and authorization before gaining access to resources. For web developers, implementing a Zero Trust approach can significantly enhance the security of websites, applications, and services.
Let’s explore how Zero Trust works, why it’s crucial for modern web development, and how to implement it to secure your digital assets in 2025.
What is the Zero Trust Security Model?
The Zero Trust Security Model is based on the idea that trust should never be assumed, regardless of where the request originates—inside or outside the organization’s network. Traditional security models rely on perimeter defenses (like firewalls) that grant access once the network is entered, assuming everything inside is trustworthy. However, with increasingly complex digital landscapes, this approach is no longer enough.
In a Zero Trust environment, every request for access, whether from users, devices, or applications, is treated as if it originates from an untrusted source. To be granted access to sensitive resources, each request must be authenticated, authorized, and continuously monitored. This model reduces the risk of data breaches and ensures that the principle of “least privilege” is enforced across the network.
Key Principles of Zero Trust Security
- Never Trust, Always Verify: The foundation of Zero Trust is that trust is never assumed, even if the request comes from inside the network. Every access request must be validated before allowing access, no matter where it originates.
- Least Privilege Access: Users, devices, and applications are only granted access to the resources they absolutely need. By limiting access, the damage from potential breaches can be minimized, as attackers will have fewer opportunities to move laterally through the network.
- Micro-Segmentation: In a Zero Trust model, the network is divided into smaller segments, each of which is treated as isolated. This helps limit the scope of potential attacks. Even if a breach occurs in one part of the network, it doesn’t automatically give attackers access to the entire system.
- Continuous Monitoring and Logging: Zero Trust requires ongoing monitoring of users, devices, and systems. Behavior analytics and real-time monitoring help detect unusual activity and identify threats before they can cause damage.
- Strong Authentication: Authentication methods like multi-factor authentication (MFA), single sign-on (SSO), and identity and access management (IAM) systems are integral to Zero Trust. These ensure that users and devices are who they claim to be before gaining access to sensitive resources.
Why Zero Trust is Critical for Web Development in 2025
As web applications and services become more complex, so do the attack surfaces that hackers can exploit. Here’s why Zero Trust is essential for modern web development:
- Increased Cyber Threats: Cyber-attacks, such as phishing, ransomware, and insider threats, continue to rise. A traditional security model that assumes internal requests are trusted leaves businesses vulnerable to these sophisticated threats. Zero Trust ensures that every request is verified, even if it comes from within the network.
- Remote Work and Bring Your Own Device (BYOD): With the rise of remote work and the increased use of personal devices in the workplace (BYOD), the perimeter-based security model is no longer viable. Zero Trust allows businesses to secure their web applications and services, regardless of where the user or device is located.
- Cloud Migration: As more businesses move to cloud-based platforms, the traditional network perimeter becomes irrelevant. Zero Trust is ideal for securing cloud environments, where data and applications are distributed across multiple locations and accessible from anywhere.
- Regulatory Compliance: Many industries face stringent data protection regulations, such as GDPR, HIPAA, and PCI-DSS. Zero Trust helps meet these requirements by ensuring that access to sensitive data is strictly controlled and monitored.
- Reducing the Impact of a Breach: If a breach occurs, Zero Trust minimizes its impact by limiting lateral movement within the network. If an attacker gains access to one part of the network, Zero Trust prevents them from easily accessing other parts, which helps mitigate the overall damage.
Implementing Zero Trust in Web Development
For web developers, integrating Zero Trust principles into your web applications involves several key steps and technologies:
1. Identity and Access Management (IAM)
IAM systems are at the heart of Zero Trust. They ensure that users are authenticated and authorized before accessing any resources. This can include:
- Multi-Factor Authentication (MFA): Enforcing MFA ensures that users need to provide more than just a password to verify their identity.
- Single Sign-On (SSO): SSO allows users to authenticate once and gain access to all necessary resources without re-authenticating for each service.
- Role-Based Access Control (RBAC): Implement RBAC to grant users access to specific resources based on their role within the organization. This ensures the principle of least privilege is followed.
2. Micro-Segmentation
Micro-segmentation divides your network and resources into smaller, isolated segments. This ensures that even if a user or device is compromised, attackers have limited access. In web development, this means isolating sensitive data and applications behind additional layers of security, and ensuring that each segment has its own strict access controls.
3. Continuous Monitoring
Real-time monitoring and logging are essential for detecting threats before they cause significant damage. By tracking user behavior and interactions within the web application, developers can spot anomalies and potential risks. Tools like Security Information and Event Management (SIEM) systems and User and Entity Behavior Analytics (UEBA) can help analyze large amounts of data and alert administrators to suspicious activity.
4. Endpoint Security
Since Zero Trust requires verification of every device, endpoint security is crucial. Devices—whether personal or corporate—must be authenticated and must meet specific security standards (such as up-to-date antivirus software) before being granted access. Web developers should ensure that their applications can integrate with endpoint protection systems.
5. Network Security
Using technologies like Virtual Private Networks (VPNs), firewalls, and Zero Trust Network Access (ZTNA) solutions, developers can ensure that users accessing web applications from different locations are authenticated and securely connected to the network. These tools help enforce the policy that access to resources is only allowed after verification, regardless of where the user is located.
Challenges of Implementing Zero Trust
While Zero Trust offers robust security, there are challenges in implementing it, especially for web developers:
- Complexity: Zero Trust requires a comprehensive and consistent approach to security. Implementing IAM, RBAC, micro-segmentation, and monitoring tools can be complex and resource-intensive.
- Integration with Legacy Systems: Many organizations have legacy systems that weren’t built with Zero Trust in mind. Integrating these systems with modern Zero Trust principles can require significant adjustments and resources.
- User Experience: The constant verification process required by Zero Trust could potentially slow down user interactions if not implemented correctly. It’s important to strike a balance between security and usability to avoid frustrating legitimate users.
Conclusion
Zero Trust is becoming a standard in web development for 2025, as the digital landscape continues to evolve and cyber threats become more sophisticated. By ensuring that every access request is verified and that only authorized users and devices can interact with critical systems, Zero Trust helps organizations significantly reduce the risk of data breaches, unauthorized access, and insider threats.
For web developers, adopting Zero Trust principles means implementing robust identity management, micro-segmentation, continuous monitoring, and endpoint security. While the implementation can be complex, the benefits in terms of securing web applications and protecting digital assets are invaluable. As cyber threats continue to evolve, Zero Trust will be an essential part of securing the future of web development.
Discover more from Rhonda Cosgriff Web Designs
Subscribe to get the latest posts sent to your email.